Her gün sizlere, piyasa değeri onlarca dolar olan bir programı tamamen ücretsiz olarak sunuyoruz!

Giveaway of the day — DiskPulse Pro 9.3.16
DiskPulse Pro 9.3.16 giveaway olarak 19 Şubat 2017 tarihinde sunulmuştu
DiskPulse is a real-time disk change monitoring solution allowing one to monitor one or more disks or directories, save reports and disk change monitoring statistics, export detected changes to a centralized SQL database, execute custom commands and send E-Mail notifications when unauthorized changes are detected in critical system files.
VIDEO TUTORIAL
Sistem Gereksinimleri:
Windows 2000/ XP/ Vista/ 7/ 8/ 8.1/ 10; Windows Server 2003-2012 R2; 500 MHz or better CPU; 256 MB of system memory; 25 MB of free disk space
Yayıncı:
FlexenseWeb sayfası:
http://www.diskpulse.com/Dosya boyutu:
10.6 MB
Fiyat:
$25.00
Öne çıkan programlar
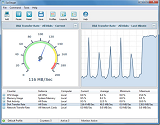
SysGauge is a free system and performance monitoring utility allowing one to monitor the CPU usage, memory usage, network transfer rate, operating system performance, the status and resource usage of running processes, file system performance, USB performance, disk read activity, disk write activity, disk read transfer rate, disk write transfer rate, disk read IOPS and disk write IOPS for individual logical disks or all physical disks installed in the computer.

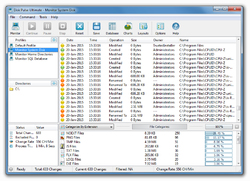

DiskPulse Pro 9.3.16 üzerine yorumlar
Please add a comment explaining the reason behind your vote.
We had diskpulse installed few months ago and removed it the next day, reason:
It created huge useless files and info that jammed our SQL server and the email server.
It happen when windows was doing updates overnight and created d-base files of all of the changes including the 0 bytes files and just the regular replacement of old files.
There were tens of thousands of files mark with red dots and marked for deletion and every single file was sent to our mail server as separate notice.
It took out IT department all day to re-load from archives to restore our SQL d-base and server.
Recording everything can be good but comes with a price to be paid down the road. It slowed the server and created useless file access record that can be detrimental to everyday use of a computer system.
Save | Cancel
And what are you supposed to do when presented with a huge number of files. !00's and 100's of file changes occur simply by say...opening up a browser.
I don't get it.
Save | Cancel
One thing is missing from the description of the product, here but also on the publisher's website : what would be the point of all that monitoring ? What are the benefits ? What type of users does this address ?
Save | Cancel